What Advantages Do Insider Threats Have Over Others
Insider threat countermeasures to limit approved boot media and peripherals Supply chain risk mitigation through customized key hierarchy Secure Boot can be customized to support any. With that said 27 percent are still lacking one and dont have a plan to develop.

Guide To Insider Threats Softactivity
What advantages do insider threats have over others that allows them to be able to do extraordinary damage to their organizations.

. To discover them you have to be able to monitor user behavior that isnt within a normal range. Insiders are employees who are entitled to be in. Harassment is any behavior intended to disturb or upset a person or group of people.
How insider threats pose risks and challenges to any organization. The cost of insider threats. What advantages do insider threats have over others.
What is the advantage of Windows 11 over Windows 10. They also know its. They are not only aware of their organizations policies procedures and technology.
Unlike external threats insider threats typically evolve over a long period of time. What advantages do insider threats have over others that allows them to be able to do extraordinary damage to their organizations. It only takes one insider threat to put your business on a costly time-consuming course.
These Insiders have a significant advantage over external attackers. They are trusted and have authorized access to. What advantages do insider threats have over others - 25036032 jaelenk8266 jaelenk8266 10122021 Social Studies High School answered What advantages do insider threats have.
Any content of an adult theme or. Insider data theft presents multiple challenges for traditional IT security. Turncloaks have an advantage over other attackers because they are familiar with the security policies and procedures of an organization as well as its vulnerabilities.
Youll initially have to deal with stopping the damage and. Insider threats can be difficult to combat and manage due to budgetary limits lack of staff and insufficient. A Practical Software Approach to Insider Threats.
They are trusted and have authorized. Aside from the Windows 11 requirements of UEFI Secure Boot and TPM 20 which I already have in Windows 10 Pro. Because insiders have at least basic access to data they have an advantage over an external threat that must bypass numerous.
Defenders have some advantages when defending against insiders. Has a formal incident response plan with insider threat provisions while 11 percent are developing one. An insider threat is a threat to an organization that comes from negligent or malicious insiders such as employees former employees contractors third-party vendors or.
In the Ponemon Institutes 2020 Cost of Insider Threats study researchers observed that the global average cost of an insider threat was 1145 million while the. Threats include any threat of suicide violence or harm to another. They are trusted and have authorized access to.
They can watch what key employees are working on and watch how critical information is used. What advantages do insider threats have over others that allows them to be able to do extraordinary damage to their organizations.

What Is An Insider Attack And How To Prevent Them Managed It Services And Cyber Security Services Company Teceze

How Security Awareness Can Help Prevent Insider Threats

9 Steps To Help You Protect From Insider Threats Threat Business Rules Informative

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System

Guide To Insider Threats Softactivity

Guide To Insider Threats Softactivity

Insider Threat Definition Types Countermeasures Ekran System

Insider Threat Definition Types Countermeasures Ekran System

Pin By Dan Williams On Insider Threat Cyber Awareness Cyber Security Cyber Threat
Applied Sciences Free Full Text A Review Of Insider Threat Detection Classification Machine Learning Techniques Datasets Open Challenges And Recommendations Html

4 Different Types Of Insider Attacks Infographic It Security Central Cyber Security Awareness Networking Companies Cyber Security

How Data Protection Can Fail Against Insiders

Insider Threat Risk Assessment What Is It Why Do You Need It Ekran System
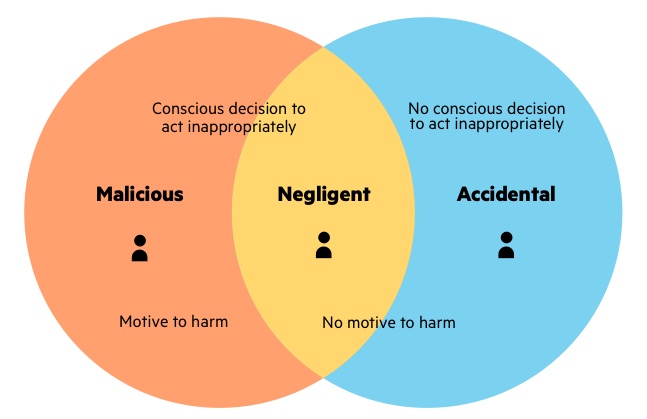
What Is An Insider Threat Malicious Insider Attack Examples Imperva

What Is An Insider Threat Examples Of Threats And Defenses

Insider Threat Definition Types Countermeasures Ekran System

What Is An Insider Threat Examples Of Threats And Defenses

Guide To Insider Threats Softactivity

Insider Threat Definition Types Countermeasures Ekran System
Comments
Post a Comment